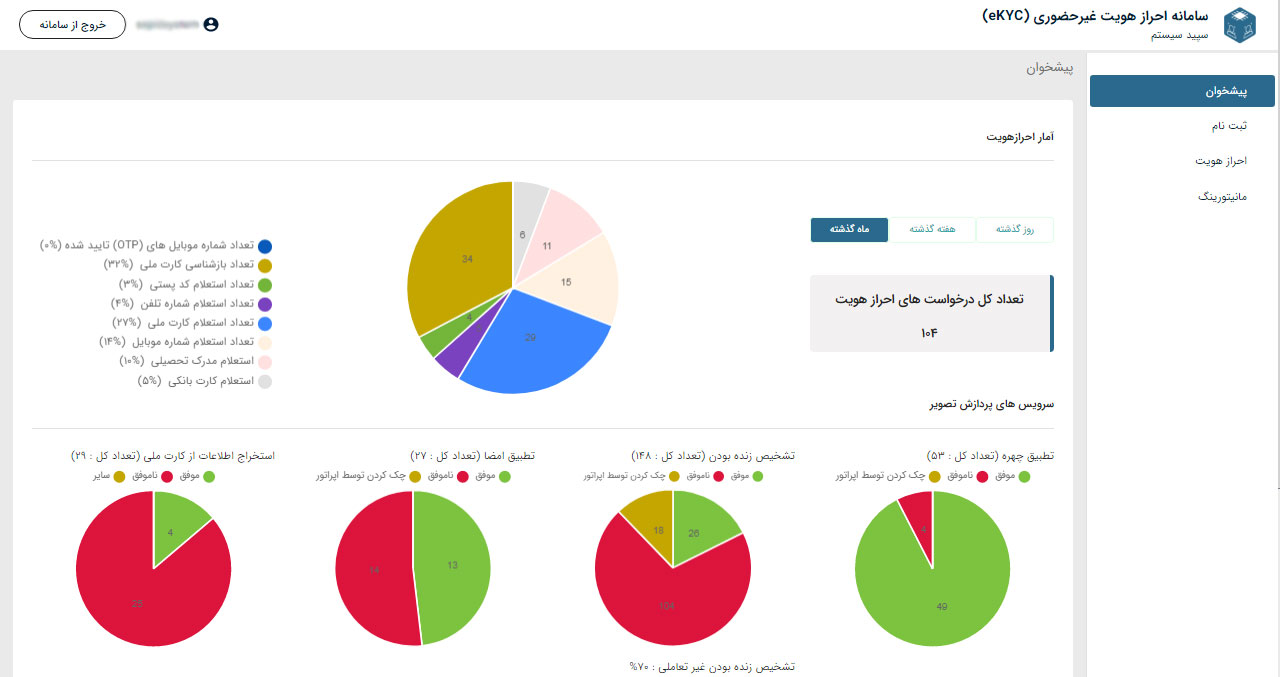
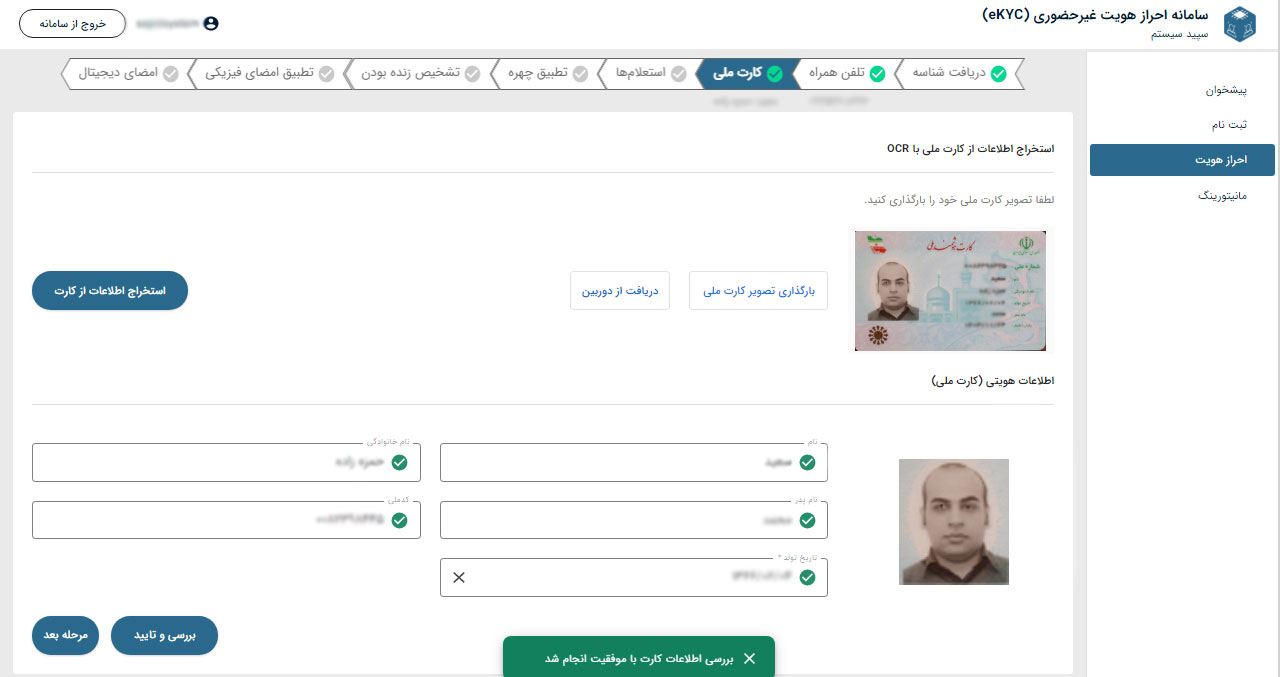
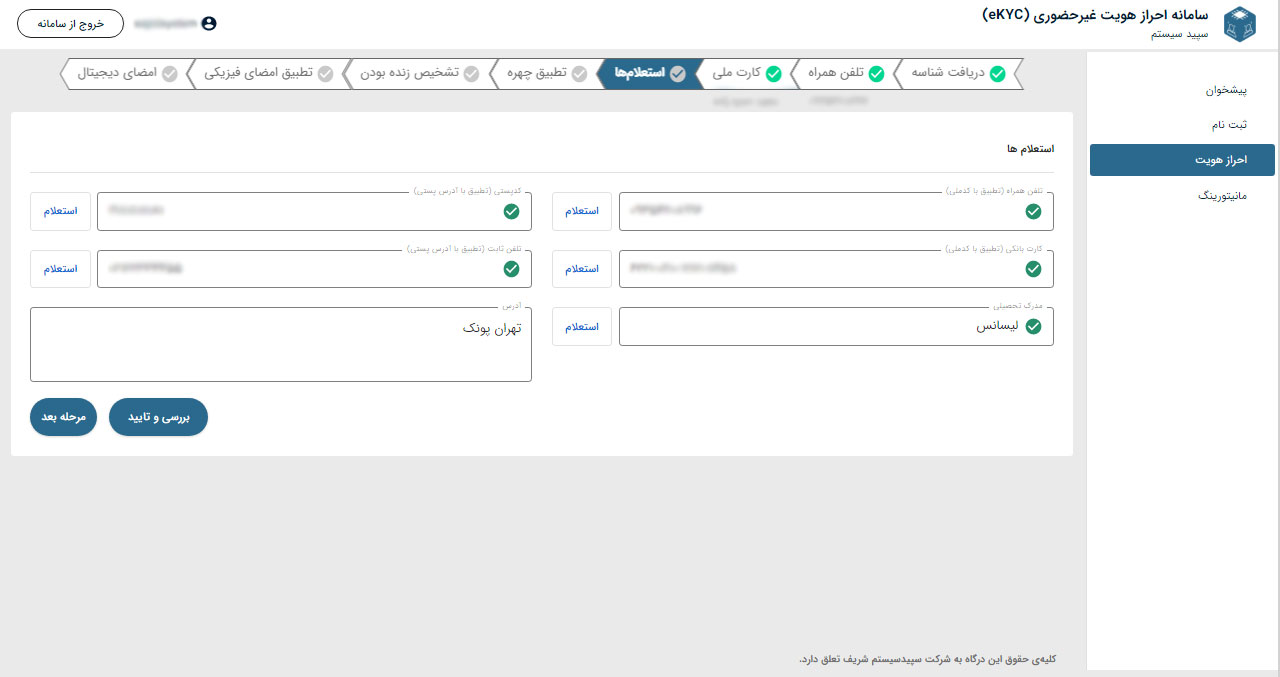
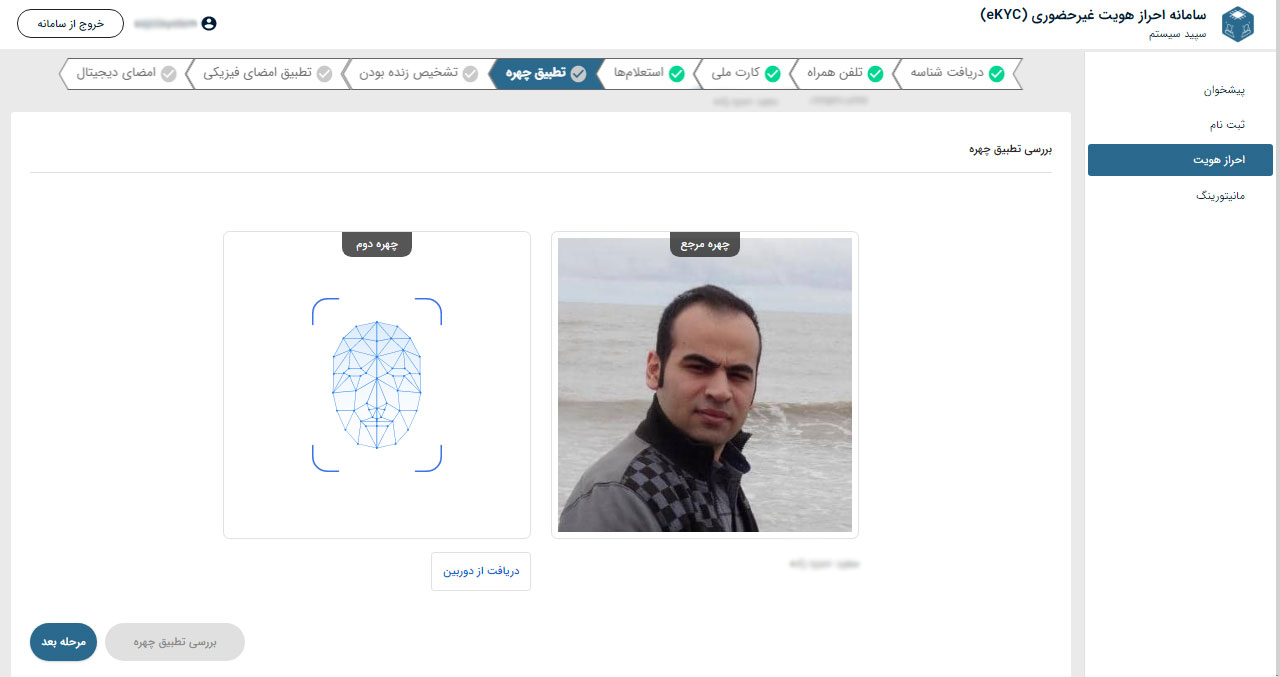
What is eKYC remote authentication?
Nowadays, remote authentication (eKYC) in order to ensure the recognition of people's identity, is needed to reduce traffic and in-person visits of people to the branches and offices of various organizations and businesses, including state institutions such as government counter offices, the judiciary (especially judicial offices), police offices (especially police+10 offices), municipality (especially urban service offices) and large businesses such as banks, mobile network operators (representative offices), insurance offices, platform and online businesses (such as home services , internet taxi and...). To accomplish this, you can use modern methods based on artificial intelligence processes, encryption algorithms and also receive online inquiries from authorized authorities.
The Sepid eKYC software system is a native product of Sepid System knowledge-based company, which as a part of this company's online authentication solution, and by using various modern methods in the field of biometric authentication and security, can provide remote authentication service in both Cloud and On-premise ways.
This software consists of different sections, which briefly include the following: