Biometric authentication
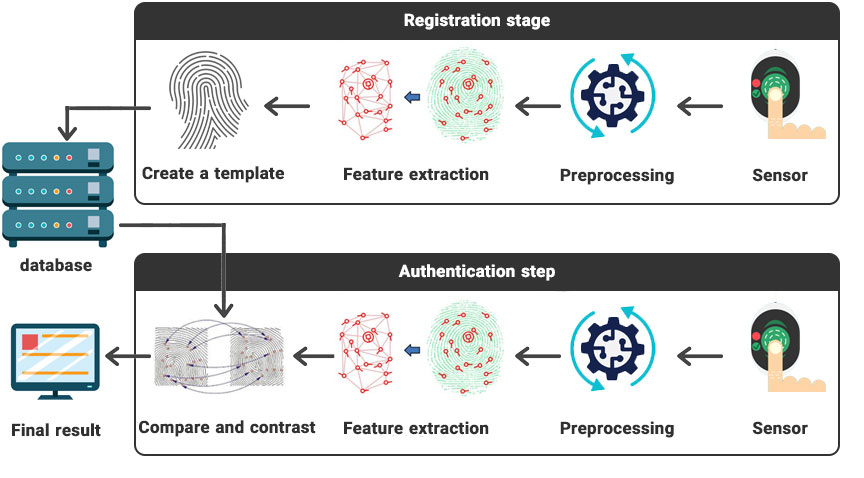
Biometric authentication, regardless of the type of measure used (fingerprint, face, signature, iris, etc.), generally has two stages: Enrollment and Identification/Verification. In the enrollment phase, biometric data such as fingerprints/face are captured by a sensor/camera and after pre-process and feature extraction, the extracted templates of each person are stored in the database. In the identification stage, the same biometric data (for example fingerprint) is received from the scanner/camera (sensor) and after pre-processing and feature extraction and template determination, it is compared and matched to the templates in the database and the identification response is determined based on it.
The subject of authentication includes two methods of verification and identification. In identity verification, the user's username and biometrics are requested, and the features of this user's biometrics are compared to the features stored in the database, and the answer is "accepted" or "rejected" in the end. This mode is called one-to-one matching. In identification, the user does not provide his username or identification number, and the system should determine the user's identity only by receiving his biometric data and comparing it to the data of all the people in the database, if the user is registered in the system. Of course, sometimes it is assumed that the user must be one of the people registered in the system, and the most similar registered person is retrieved from the database as an output. This mode is also called matching 1 to N.
Using a smart card for authentication and access control is one of the common ways to increase the level of security, in which the identity information of a person is stored inside smart cards, and in some cases, the authentication process itself is carried out inside these cards. If this approach is combined with biometrics methods such as fingerprint recognition and face recognition, it creates a safe and secure solution. The national smart ID card, which stores personal identity information along with biometric parameters such as fingerprints, is one of the common examples of this issue. Other smart cards such as driving license and passports are examples of this authentication method.
Verification based on fingerprint, face, signature and iris
In this case, the biometric capability based on fingerprint, face, signature or iris (or their combination) is used to confirm the identity of people. In this method, which is also called 1:1 matching, in addition to receiving one (or more) of the biometric measures, an identifier is also taken from the person, which expresses the person's claim about who he is. Then the identity verification unit compares the person's parameters to the corresponding templates in the database and provides a confirmation or rejection answer. The Sepid System identity verification solution, using hardware equipment related to various biometrics for fingerprints, face and iris, can be installed and set up in the form of centralized management, and large organizations and companies can use them in all their branches in a wide geographical area (in the country or the world).
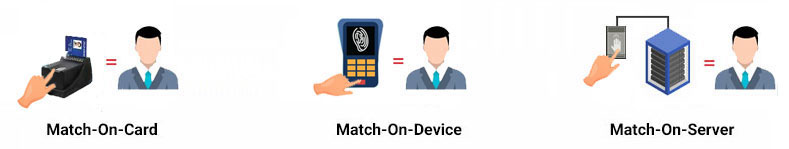
Also, this method can be used in three ways: matching on the server (Match-On-Server), matching on the device (Match-On-Device) and matching on the card (Match-On-Card). In matching on the server, the devices receiving metrics send them to the server and the authentication process is done on the central server, but in the mode of matching on the device, the process of identifying and matching is done on the device itself (fingerprint recognition or face recognition such as time and attendance devices). In matching on the card, smart cards are used to store or match the biometric identity on the card. This solution uses the SepidStar software platform for managing hardware and information. It also uses the Sepid System artificial intelligence services such as fingerprint recognition and face recognition.
Biometrics identification (ABIS: Automated Biometric Identification System)
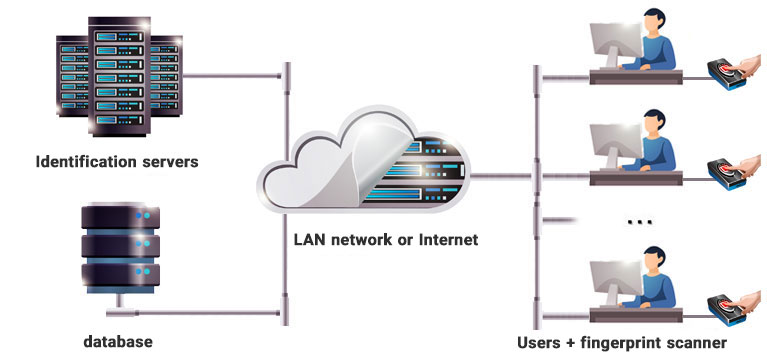
The advantage of detecting people with an approach based on identification is that the person only provides his biological identifier, such as a fingerprint or face, and the system automatically searches among the people in the database and identifies the person. This mode is more convenient for users due to not needing a personal ID, and most authentication systems are moving towards this approach. In the ABIS system identification solution, searching for various biometric parameters such as a person's face or fingerprint among several million samples in a short time and with optimal accuracy is possible. In case we only use the fingerprint parameter, a more limited version of ABIS called AFIS is used.
This solution has various uses, including the following:
- Registering and controlling the movement of people in companies and organizations to control access and provide the possibility of time and attendance
- Automatic control of borders (ABC) and airports to authenticate travelers and tourists
- Security applications and finding criminals, smugglers, terrorists, etc.
With many years of experience in setting up biometric-based systems and cooperation with foreign partners, Sepid System provides ABIS solution for organizations, companies and departments. Saving and retrieving identity metrics such as face, fingerprint and signature online (scanning) or offline (such as a fingerprint taken from a crime scene or in ink or with a photo of a person's face) by installing and setting up the system in a centralized way is provided in this solution. This system uses the optimal methods of biometric identification, such as fingerprint recognition, face recognition and signature recognition, which provides high speed and accuracy for search among a large number (several million) of biometric patterns.
Biometric identification on smart card (MOC: Match-On-Card)
In this case, which is part of Sepid System Company's authentication solution, the advantage of biometric technology and smart cards (such as smart national ID card, electronic passport and smart driving license) is used to increase the level of security in movement control and access control applications. In the biometric-based method with a smart card (BSC: Biometric Smart Card), people's identity metrics (such as fingerprints or faces) are stored on the smart card, and at the time of authentication, the individual's fingerprints/face are sent to the card and the process of matching the identity metrics and identity verification and access permission are done on the card.
In the smart card identification method, there are four methods to combine Biometric and Smart Card technologies, which include Template-On-Card (TOC), Match-On-Card (MOC), Work-Sharing-On-Card and System-On-Card (SOC), the details of which you can see in the review article on biometric methods in smart cards. Among the mentioned methods, SOC is more secure than other methods and TOC has the lowest security, but due to the high cost of SOC (because all the necessary equipment for authentication is provided with the card), this method can only be used in limited applications. Therefore, among these four approaches, the matching on card (MOC) method is more common due to its high level of security and cheapness.
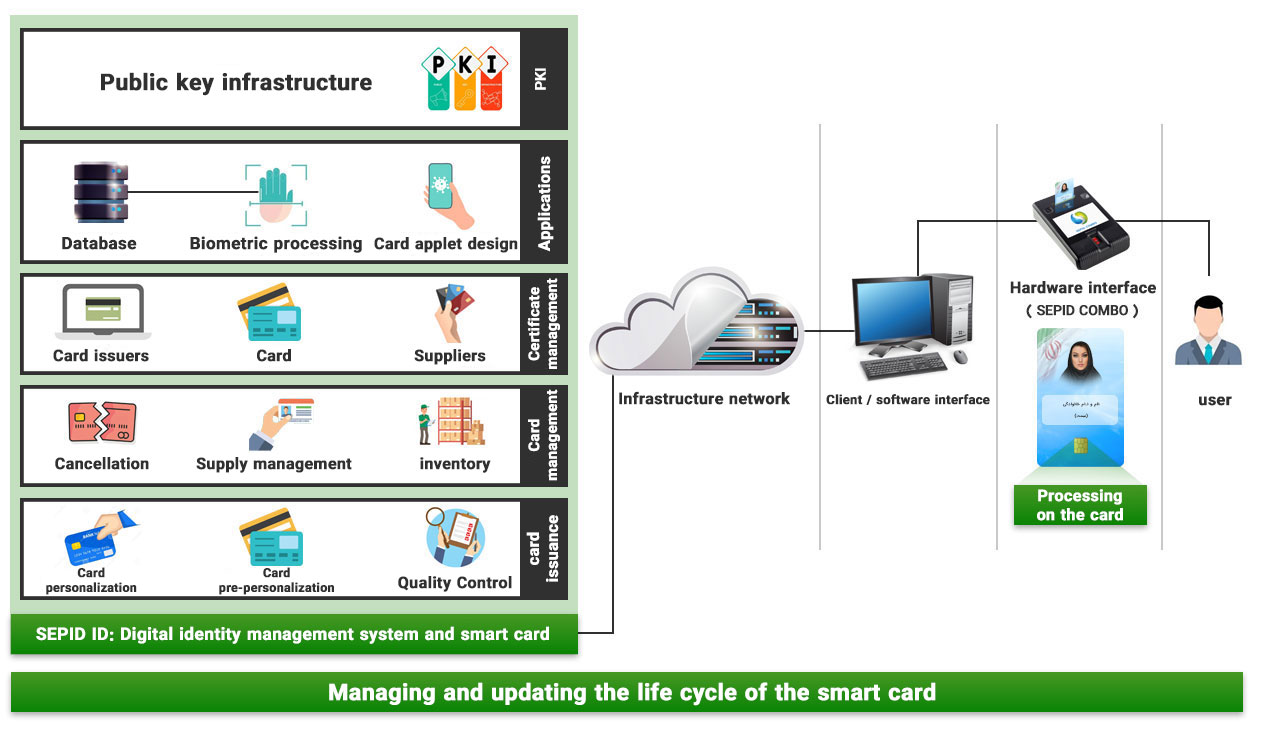
Using local knowledge, Sepid System has developed a card-based fingerprint and face authentication solution with MOC method, which includes all subsystems and different programs (picture below). This solution includes the Sepid ID software system for managing the life cycle of the card from card storage to issuing the card (including pre-personalization, personalization) and managing the applications on the card side (applets) and supporting it after issuance (such as changing the password and. ..) as well as card side programs (applets) including identification applet, fingerprint matching and face matching on the card. Also, its hardware part includes fingerprint scanners, card readers and face recognition cameras, or multi-purpose devices for this purpose, such as the Sepid Combo multi-purpose authentication device.
Applications of smart card-based biometric solution
Smart card-based biometric solution with MOC method can be used in various applications that require secure, fast and easy access, including:
- Banking services for employees and managers access to banking systems or individuals to online accounts and services and payments and money transfers
- Use of national smart ID card for authentication, for example, in banking affairs
- Health and insurance smart card
- Digital accesses, logins to computers or other computer systems
- Passports and automatic authentication at borders and airports (Iranians or foreign nationals)
- Polling and voting cards (authentication systems in elections)
Advantages of card-based biometric solution
- Higher security due to the storage of biometric information (fingerprint, face, iris, etc.) and identity matching processes inside the card and preventing eavesdropping and copying
- Two-factor authentication by sending a challenging code between the terminal (computer) and the card
- On-card decision making to increase security by matching patterns and deciding whether to approve or reject on-card authentication
- High accuracy in pattern matching using the most up-to-date machine learning and artificial intelligence methods
- Flexibility and usability in different applications with the possibility of customization